An Introduction to OP-TEE
2017 年 08 月 25 日 ソリューション統括部
OP-TEE is designed primarily to rely on the ARM TrustZone technology as the underlying hardware isolation mechanism. However, it has been structured to be compatible with any isolation technology suitable for the TEE concept and goals, such as running as a virtual machine or on a dedicated CPU. Before we deep dive into OP-TEE, we should be clear on what is TEE itself.
What is Trusted Execution Environment (TEE)?
TEE is basically an Isolated Execution Environment for application or OS or Firmware. It can run alongside a "Rich OS"'s like Android, Ubuntu. As the name suggests TEE provides higher levels of security than the Rich OS. This provides much secured trusted services to applications running in Rich OS for enhancing the security. TEE offers a high level of protection against attacks from the rich OS.
TEE normally has a very Small footprint which is a big advantage for smaller systems. It will give the permission to execute only trusted/authorized software. There is a guarantee that Sensitive data will be protected from the rest of the application processor software and from the outside world. The Below Block diagram shows the architecture of TEE.
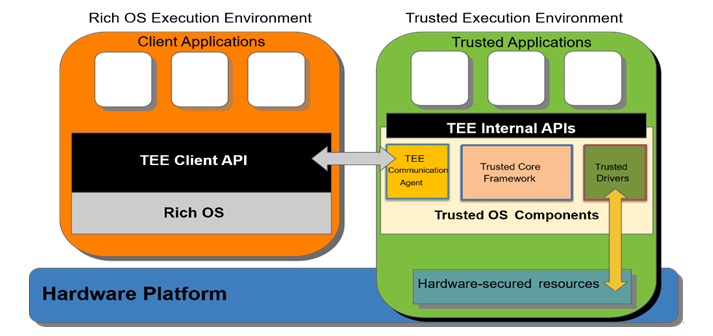
Key Concepts of TEE
The Following Figure shows the key concept of TEE. It can be broadly divided into four. Context, session, command and shared memory are those four.
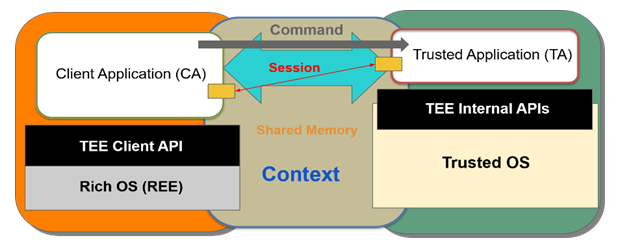
Context here is the connection between client application and Trusted OS. Session is the operation connection between Client application and trusted application. Command is the unit of communication between Client application and trusted application. These concepts together constitutes TEE.
What is OP-TEE?
OP-TEE is an Open Source TEE and is the result of collaboration work between STMicroelectronics and Linaro Security Working Group. It contains the complete stack from normal world client API's (optee_client), the Linux kernel TEE driver (optee_linux driver), the Trusted OS + the secure monitor (optee_os) and the test suite (xtest).
What are the Components of OP-TEE?
There are three major components with OP-TEE, which can be divided into OP-TEE client,
OP-TEE Linux kernel driver and OP-TEE trusted OS. OP-TEE client is the API that is running in the normal world space to support OP-TEE, whereas OP-TEE Linux kernel driver is the one that handles the communication between normal world user space and secure world and OP-TEE Trusted OS is the one who secures the trusted world. OP-TEE trusted OS is having two parts namely OP-TEE core and OP-TEE libraries. OP-TEE core will be executed in ARM CPU privileged mode. OP-TEE libraries are the static Libraries that to be used by the trusted applications.
OP-TEE Architecture
As we have seen earlier the overall system can be divided into two parts Normal and secure world. Both together comprises OP-TEE. Please find the figure below for more understanding
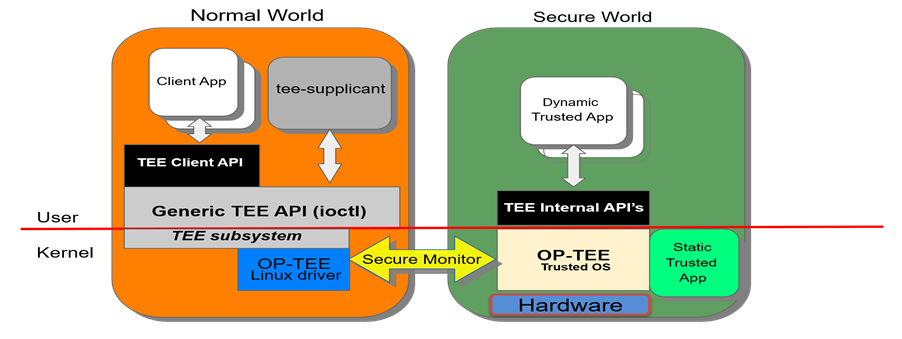
From this architecture, the normal world kernel subsystem has three major components. The first one is TEE subsystem. TEE subsystem is the one who manages the shared memory and is responsible in providing a generic API as IOCTL. tee-supplicant is the next component which is working as the helper process for Trusted execution Environment. OP-TEE driver is the one who takes care of command forwarding from the clients to OP-TEE. Also OP-TEE driver manages the RPC requests from OP-TEE to the supplicant.
What is Trusted Apps in Secure world?
Trusted apps are the applications running in the secure world. Trusted apps can be broadly divided into static apps and dynamic apps. Static apps are those apps which will be running in kernel mode, while dynamic apps are the apps stored in file system. Dynamic apps will be loaded by OP-TEE with the help of tee-supplicant.
How will OP-TEE do communication and scheduling?
The communication to the trusted Environment is controlled either by SMC or by some exceptions by FIQ. When a command arrives to the secure world the activity will be allocated to a special thread (if available). It will return to the normal world after completion of execution or in case of an IRQ event.
Posted by vi
記事カテゴリ別新着一覧
Vigiles サポート
Vigiles ファーストステップガイド 4 「SBOM ダッシュボードの使い方」
2025 年 05 月 14 日 Vigiles サポート
Vigiles ファーストステップガイド 3 「Build root 環境の Vigiles 導入手順」
2024 年 09 月 02 日 Vigiles サポート
Vigiles ファーストステップガイド 2 「Yocto 環境への Vigiles 導入手順」
2024 年 03 月 01 日 Vigiles サポート
Yocto Project よもやま話
Yocto よもやま話 第 16 回「Yocto Project SUMMIT 2024/12」
2025 年 06 月 04 日 Yocto Project よもやま話
Yocto よもやま話 第 15 回 「Yocto 5.0 Scarthgap リリース」
2025 年 06 月 03 日 Yocto Project よもやま話
Yocto よもやま話 第 14 回 「Yocto 4.3 Nanbield リリース」
2024 年 03 月 26 日 Yocto Project よもやま話
Linux 技術ネタ
RISC-Vについて学ぶ-後編
2024 年 01 月 10 日 Linux 技術ネタ
RISC-Vについて学ぶ-前編
2023 年 12 月 12 日 Linux 技術ネタ
デバイスツリーとサウンド設定(widgets, routing)について学ぶ:後編
2023 年 03 月 31 日 Linux 技術ネタ
イベントレポート
EdgeTech+ 2025 出展レポート
2025 年 12 月 01 日 イベントレポート
EdgeTech+ West 2025 出展レポート
2025 年 08 月 08 日 イベントレポート
EdgeTech+ 2024 出展レポート
2024 年 12 月 06 日 イベントレポート
リクルート
新卒採用、絶賛募集中!
2025 年 04 月 01 日 リクルート
新卒採用、絶賛募集中!
2023 年 05 月 30 日 リクルート
大しごとーく & オープン・カンパニー in 信州 2022
2022 年 12 月 27 日 リクルート
信州リネオ便り
2026年 明けましておめでとうございます
2026 年 01 月 06 日 信州リネオ便り
2025年忘年会を行いました
2025 年 12 月 23 日 信州リネオ便り
上半期打ち上げ懇親会を行いました
2025 年 10 月 06 日 信州リネオ便り
ソリューション統括部
シリコンバレー探検記 2019 ~番外編~
2019 年 12 月 10 日 ソリューション統括部
シリコンバレー探検記 2019 ~後編~
2019 年 12 月 10 日 ソリューション統括部
シリコンバレー探検記 2019 ~前編~
2019 年 12 月 10 日 ソリューション統括部
マーケティング統括部
大成功決起大会!!(ET2019)
2019 年 12 月 13 日 マーケティング統括部
ESEC 2019 決起大会
2019 年 04 月 25 日 マーケティング統括部
シリコンバレー探検記 その 2
2018 年 12 月 18 日 マーケティング統括部






















